In this final blog post on the methods we can use to work with delegated permissions against Microsoft Graph we are going to take a look at a more simple method of working with delegated permissions against Microsoft Graph using the HTTP with Azure AD connector in Power Platform.
Are you enjoying this content on Microsoft Graph? Make sure you’re subscribed to my blog to continue to get my posts throughout the rest of this series, and daily for 2023.
SubscribeHTTP with Azure AD Connector
So very simply, we can use the HTTP with Azure AD connector in our Power Apps and Power Automate flows to interact with resources that we can get to with Azure AD secured APIs, using delegated permissions. So we can only execute operations for things we as a user have permissions to do.
Using the connector in a flow to delete an application
So lets look at a simple scenario. I have an old redundant application in Azure AD which I want to remove from my tenant. I can do this using the Microsoft Graph API. Let’s try to achieve this using two different users, the HTTP with Azure AD connector in Power Automate, and the Microsoft Graph API.
The reason I will attempt this with two different users is to demonstrate how the connector works with delegated permissions to only authorise operations that the user in context has permissions to execute normally.
Attempting to delete the application without the user having permissions
So let’s first assess the behaviour using a user account which doesn’t have any Azure AD admin roles, and doesn’t own the application.
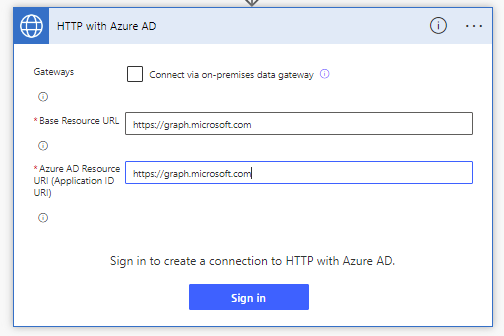
I’m going to create a new cloud flow, and add the HTTP with Azure AD, invoke a HTTP request step, and I’ll need to start by creating a connection.
For both inputs I’ll add the base URL of the API, https://graph.microsoft.com and then I’ll create the connection.
Now all I need to do to work with this request step is fill in the request I want to make towards the Graph API. I don’t need to worry about doing anything at all extra with authentication.
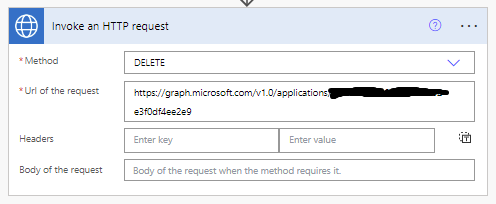
For my request URL to delete my application I’m going to use the following…
https://graph.microsoft.com/v1.0/applications/application
To delete this application, I will set the method of my request to DELETE
Let’s see how this works now by testing our flow. Remember I’m doing this at the moment using the users connection who doesn’t have access to this resource in Azure AD as an owner, and who doesn’t have any Azure AD administrative roles.
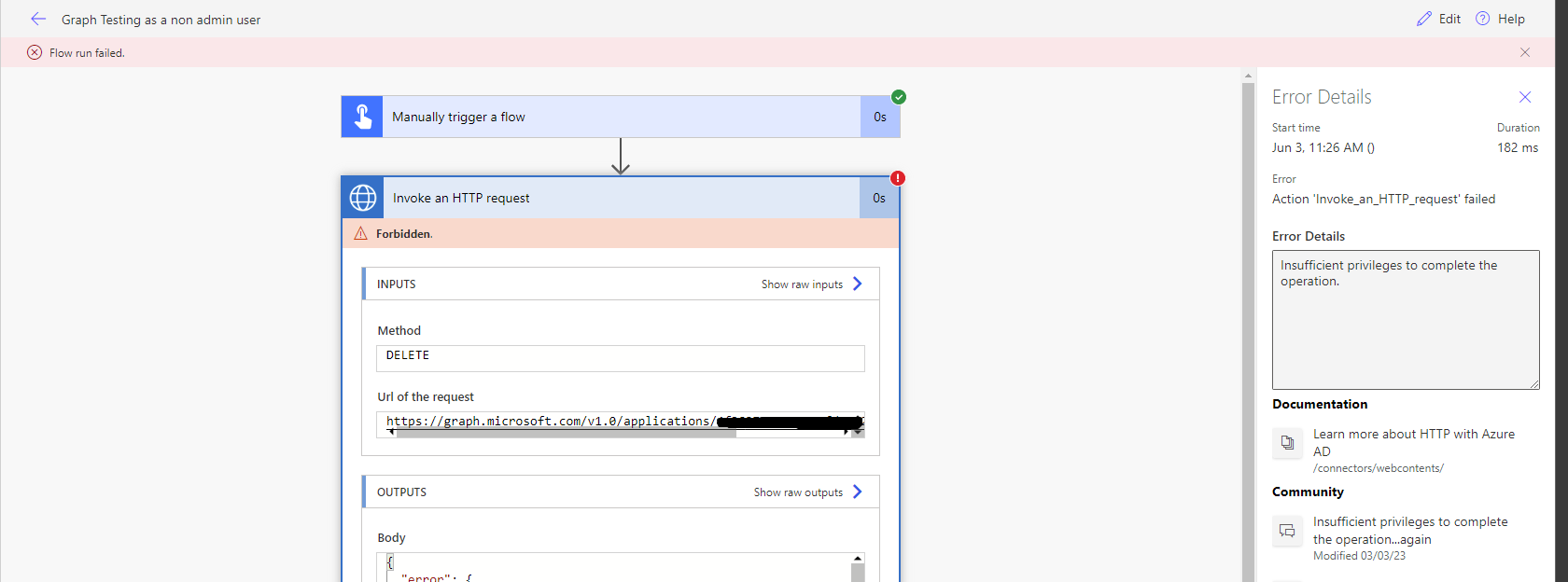
Attempting to delete the application with a user who has permissions
I’m now going to complete the exact same set of steps above but with a users connection who has permissions against the resource in Azure AD. Let’s just test this flow and see how it works!
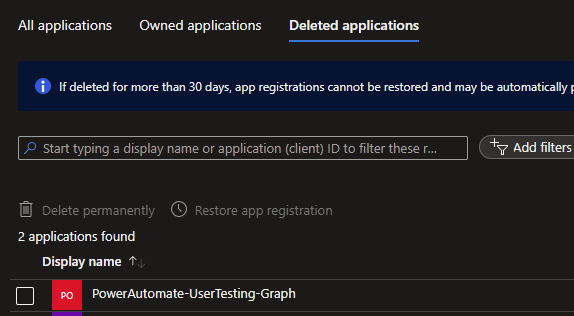
Now with my user who has permissions in Azure AD, working with my delegated permissions against Microsoft Graph by using this HTTP with Azure AD step, you can see that my flow has run successfully and my app registration has been deleted.
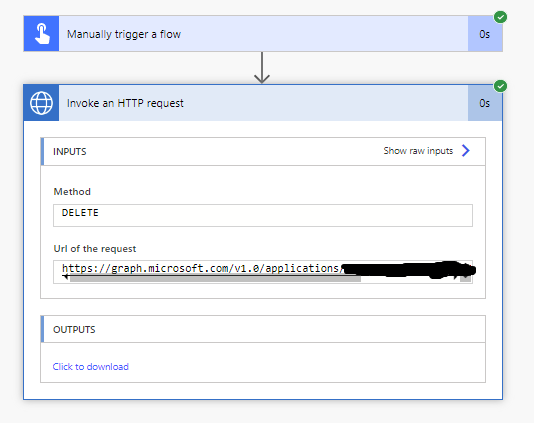
Here is my deleted application.
Overview
Hopefully you’ve enjoyed this content on the different methods to working with delegated permissions against Microsoft Graph. Next we’ll move onto working with application permissions and a bit more about this in contrast to delegated permissions. Make sure you’ve subscribed to my blog to get these upcoming posts directly in your inbox.
